What is a Behavioural Roadmap and Why Should You Use One?
In complex settings, good controls on paper still fail on site. Small shortcuts become the norm; tension at a gate becomes a stoppage. A behavioural roadmap links systems thinking with analytical thinking: first see how risk flows through the organisation and its interfaces, then fix the things that can change daily behaviour and lead to bad decisions. The result is practical: fewer stoppages, earlier signals, and security technology that can provide real insights.
Who it’s for
Designed for senior security leaders and readily usable by Social Performance and ESG teams. It also helps operations staff, supply chain, and HR coordinate around the same priorities.
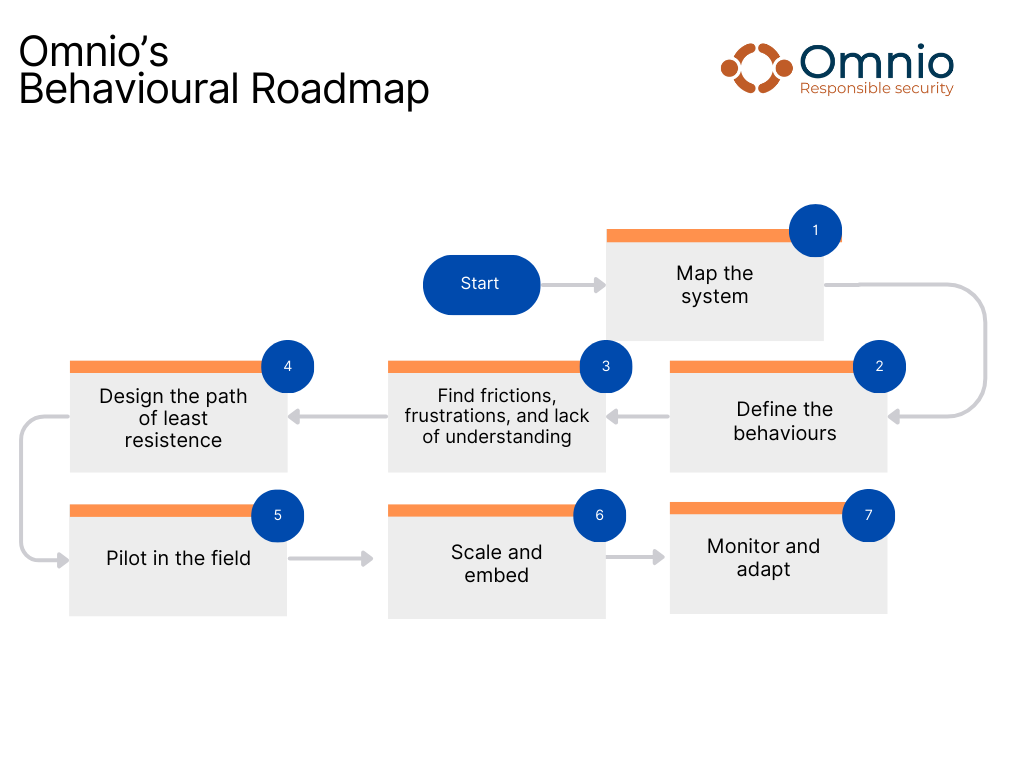
The seven stages
Map the system – ZOOM OUT
Build a plain system map: people, incentives, controls, technology, supply change, regulations and external stakeholders - host communities, state forces, contractors. Overlay critical assets with the current threat analysis to spot potential vulnerabilities. Stage one in full detail.
Define the behaviours
Look at the systems and where the people fit. Be specific about who must do what, where, and how they may come under pressure. Find the places where behaviours may undermine the system. Context is key – think about pressure, not just a normal day. Consider how threat information is used and be attuned to risk habituation – it was fine today, it will be fine tomorrow.
Find frictions, frustrations and lack of understanding – ZOOM IN
Observe work as done. Use a short checklist to look for time pressure, ambiguity and friction. Scan data—robust performance indicators, grievances and other non‑security reporting, access‑control data, incident mapping, threat picture, and sentiment analysis. This is where we locate patterns so we can fix systems holistically.
Design the path of least resistance
Work across three tracks in parallel.
a) Systems and controls:
Make the secure way the easy way - layout, UI, tech deployment, procedures.
b) Processes:
Make the right way the easy way - simplify steps under pressure; clarify escalation routes.
c) Information and Communication:
Make the human way the easy way - cues, briefings and cultural pointers at the interfaces with all your stakeholders, internal and external. Tell a story with your threat analysis and paint the actionable insights.
Pilot the field
Run a short, time‑boxed trial at one site, gate, community meeting, shift or route. Where change is easy to reverse, use A/B pilots; where it is hard to reverse, consider workshop‑led simulations first. Make sure you measure impact honestly – look for bad feedback not a pat on the back. If it doesn’t land – think again.
Scale and embed
Scale what works using a ‘training‑by‑doing’ method in these four steps:
a) Identify the people that do the task – DO NOT USE YOUR BEST PEOPLE
b) Identify the single person that is accountable for the task – DO NOT USE YOUR BEST MANAGER
c) Know the people whose input you need – don’t just ask – listen. DO NOT LISTEN TO THE LOUDEST VOICES.
d) Keep the people that need to know informed. GET BUY-IN FIRST
A great example of this could be… You find friction or work-arounds in your access control process, here’s how you scale and embed:
a) Your Access Control personnel do the task – A/B test in two areas?
b) Your Site Security Manager owns the task
c) Operations, Social Performance, Supply Chain and HR should have input to the changes
d) Keep senior managers and users of the system informed of the changes and subsequent results
7. Monitor and adapt
Track a carefully selected set of indicators – seek negative feedback not a pat on the back. This results in a reduction on incidents and stoppages, early warnings through new channels, access control efficacy, improved threat analysis and better technology-based reporting. Refresh regularly and adjust early – don’t talk – experiment.
A short observation checklist
Is the safe way the easy way under time pressure?
Are steps clear at 3am, when tensions escalate or a threat is identified?
Where do people wait, re‑enter data, or double‑handle? Remove the friction.
Do supervisors escalate “soft signals”, or does, potentially bad news, travel slowly?
Do contractors see why steps matter? Does your process make sense?
Are protocols clear to all? Any language or expectation gaps?
Do briefings use plain language and the right channels?
Does the tech help the user? If not, change it.
What gets measured or praised here? Align incentives with the behaviour.
Incentives don’t sanction
Decision gates and governance
To keep momentum and avoid drift, use explicit decision points:
After mapping - identify improvements that are easily reversed and make them.
After defining behaviours prioritise what are the 3 – 5 potentially biggest wins and find the simplest solutions
Test them – look for A/B trials wherever possible – always think – could this scale – DO NOT USE YOUR BEST PEOPLE FOR THE TRIAL.
After testing, decide to scale, redesign or stop.
Before you scale, confirm the ownership and support.
Review, refresh, retry
Repeat
Evidence and outcomes
Headline outcomes: reduced incidents and stoppages; more external signal flow; improved KPIs (access compliance, muster speed, fewer flashpoints at external stakeholder interfaces).
Secondary benefits: improved performance during high tempo periods, better contractor onboarding, higher confidence in site leadership.
Final thought
Security is not about reacting. It’s about anticipating, influencing, and empowering. It’s about seeing risk where others don’t. Omnio knows, and science shows, that a secure, inclusive environment that respects the rights and well-being of everyone involved creates a lasting positive impact and better security.
By combining culture‑centred behavioural insights with deep regional knowledge and intelligence, we help executives not merely survive shocks, but build organisational resilience that thrives: even under pressure.
About Omnio Services
We are trusted partners to organisations seeking proactive security solutions. With 40 years of combined global experience, behavioural science methodology, and regional risk intelligence, we make sophisticated security practical - helping keep operations running, reputations intact, and profitability resilient. If you’d like to explore how we can help your organisation reduce risk, enhance visibility, and protect operational continuity, just reach out.