Omnio’s Behavioural Roadmap: Step 1
Who is the Behavioural Roadmap for?
A behavioural roadmap links systems-thinking with analytical-thinking: first see how risk flows through your organisation and its interfaces, then fix the things that can change daily behaviour and lead to bad decisions. The result is practical: fewer stoppages, earlier signals, and security technology that can provide real insights.
Designed for senior security leaders and readily usable by Social Performance and ESG teams. It also helps operations staff, supply chain, and HR coordinate around the same priorities.
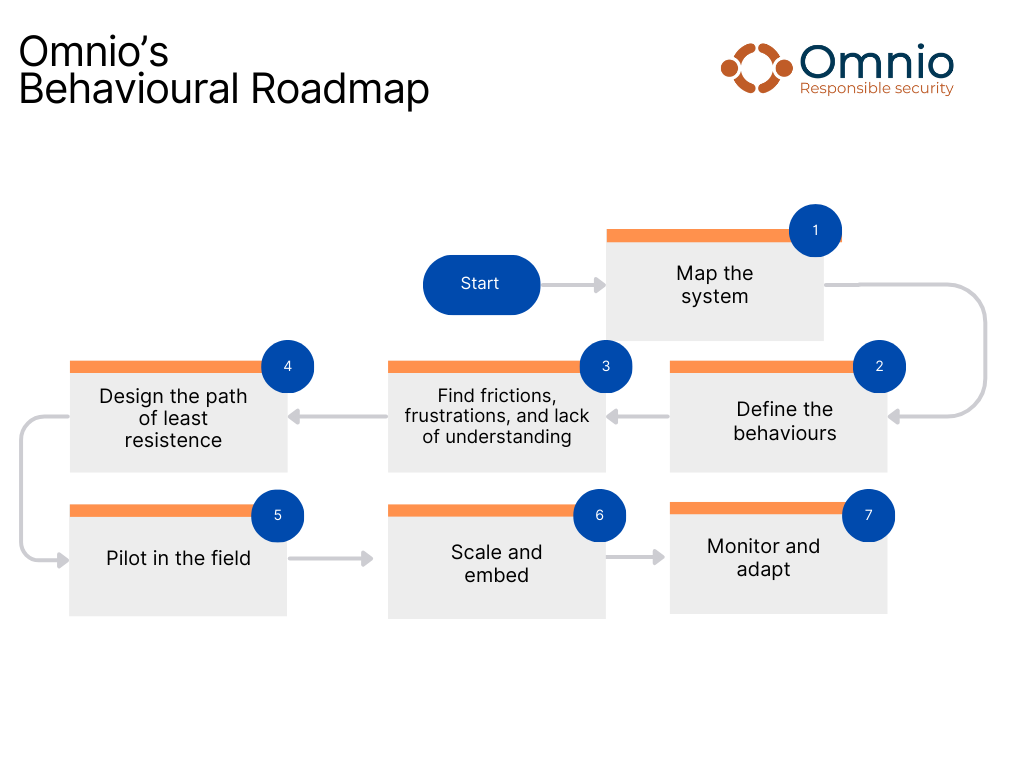
There are seven steps to our Behavioural Roadmap.
Step 1: Map the system
Before analysing risks or designing interventions, you must first understand the ecosystem your security sits within. Behavioural vulnerabilities rarely originate from one failure — they emerge from systems of people, incentives, pressures, tools, rules, and real-world constraints.
It is vital to be curious and open minded while you build your high-level system map.
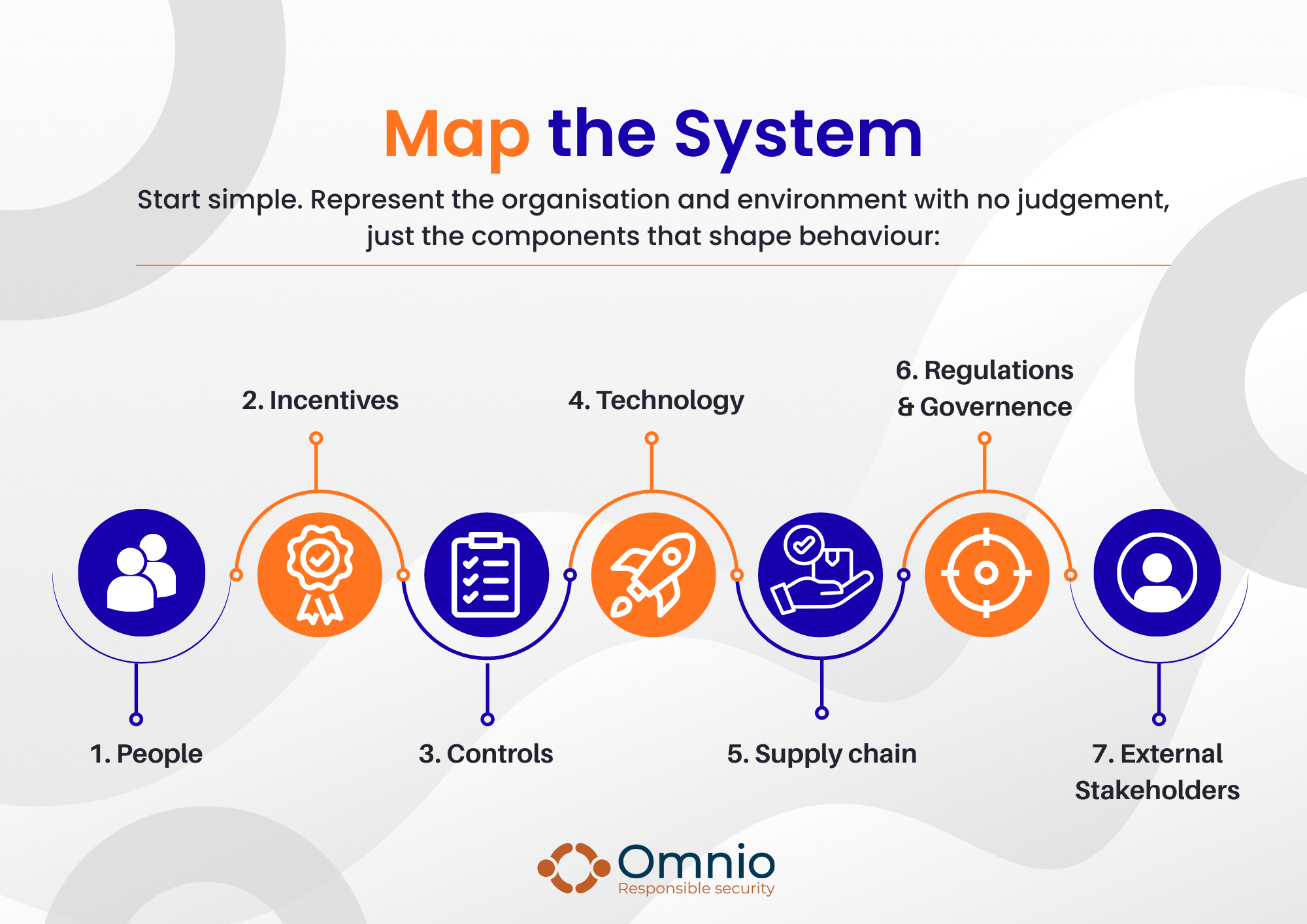
1. Build a System Map
Start simple. Represent the organisation and environment with no judgement, just the components that shape behaviour:
1.1 People
Frontline teams
Supervisors and leadership
Contractors and subcontractors
Third-party vendors
High-access staff (Operations, security, operations, Safety, IT)
1.2 Incentives
What people are rewarded for (speed, output, customer satisfaction, keeping the peace)
What they are penalised for (delays, escalating issues, stopping work)
Informal norms (“just get it done”, “don’t bother the boss”, “keep trucks moving”)
1.3 Controls
Physical (access, barriers, surveillance)
Digital (permissions, authentication, logging)
Procedural (SOPs, checklists, escalation routes)
Cultural (challenge culture, peer norms, leadership signals)
1.4 Technology
User interfaces and usability
Systems that people routinely bypass
Legacy systems that create workarounds
Alerts, alarms, and their real-world credibility
1.5 Supply Chain
Contractors
Local labour
Transport/logistics partners
Security subcontractors
Vulnerable stages
1.6 Regulations and Governance
National laws
Industry standards
Local enforcement realities
Reporting requirements
Oversight and audit systems
1.7 External Stakeholders
Communities
Local authorities and state forces
Competitors
2. Overlay Critical Assets and Threat Analysis
Once the system is mapped, add:
2.1 Critical Assets
People (staff, contractors)
Critical operational assets
2.2 Threat Analysis
Place your current threat picture directly on top of the system map:
Human threats (insider action, opportunistic theft, organised crime, activism, terrorism)
Community tensions
Operational hazards
Political and security volatility
Misaligned contractor incentives
2.3 Spot Vulnerabilities
Vulnerabilities appear where threats intersect with weak points:
A contractor with broad access but weak oversight
A community grievance that increases social-engineering risk
A process designed around convenience, not control
A team under output pressure who bypass checks
A technical control that conflicts with usability and gets ignored
What you end up with is a behaviourally aware, whole-system view of where risk genuinely lives — not where policy assumes it lives.
Here’s four (real-world inspired) narratives
The Oil Site, Where the Weakest Link Wasn’t in The Fence
A major O&G operator in West Africa invested heavily in internal physical security — cameras, ID systems, access points. On paper, the site was well-protected.
But when they zoomed out and mapped the system, they realised:
A contracted water tanker driver had access through multiple checkpoints.
He was paid per load, creating strong incentives to move quickly.
Local guards, familiar with him over years, waved him through without full checks.
Community tensions meant he was under pressure to smuggle items for relatives.
He eventually transported small stolen components out of the site — not maliciously at first, but opportunistically. The system map showed that the vulnerability didn't come from the perimeter or the technology — it came from incentives in the supply chain and security staff familiarity.
The Data Centre That Discovered Usability Was the Real Security Gap
A European data centre kept suffering from repeated access mistakes — piggybacking, forgotten passes, shared credentials. Leadership assumed staff needed “more training”.
When they zoomed out, the map showed:
Engineers moved between rooms up to 20 times per shift.
The access system required a repeated, slow, full authentication each time.
Under time pressure, engineers routinely propped doors open to maintain workflow.
Supervisors encouraged meeting SLAs over compliance.
This revealed that secure behaviour was incompatible with operational design. Fixing security meant redesigning the system (faster access controls, staged zones, workflow-aligned authentication), not punishing staff.
The Mining Company That Underestimated Community Influence
A mining firm in Latin America wanted to understand recurring security incidents around their remote camps. Zooming out showed:
Local community leaders felt excluded from hiring decisions.
This grievance increased the willingness of young men to participate in sabotage, theft, or pressure tactics.
Guards recruited from neighbouring towns felt unsafe challenging locals they knew socially.
A growing underground economy around stolen fuel and other itms created vested interests.
The vulnerability was not the perimeter fence — it was the relationship between the site and its host community, driving behaviours that bypassed controls.
This insight shifted their security approach from purely technical to behavioural + social licence management.
The Logistics Company That Found Its Risk in Franchise Incentives
A global logistics firm suffered repeated security failures at certain depots (losses, unauthorised access, cargo tampering).
A plain system map made the issue clear:
These depots were run by franchise partners, paid per parcel processed.
Background checks were inconsistently implemented.
Temporary labour had high turnover and minimal vetting.
Local managers favoured “speed and throughput” over compliance.
Contractors often shared access cards to keep vehicles moving.
Security incidents weren’t due to a lack of rules — they were due to a misaligned incentive structure that made non-compliance rational.
After mapping the system, the company changed KPIs, enforced standardised vetting, and embedded behavioural expectations directly into franchise contracts.
Final thought
Security is not about reacting. It’s about anticipating, influencing, and empowering. It’s about seeing risk where others don’t. Omnio knows, and science shows, that a secure, inclusive environment that respects the rights and well-being of everyone involved creates a lasting positive impact and better security.
By combining culture‑centred behavioural insights with deep regional knowledge and intelligence, we help executives not merely survive shocks, but build organisational resilience that thrives: even under pressure.
About Omnio Services
We are trusted partners to organisations seeking proactive security risk management solutions and cultural change. With 40 years of combined global experience, behavioural science methodology, and regional risk intelligence, we make sophisticated security practical - helping keep operations running, reputations intact, and profitability resilient. If you’d like to explore how we can help your organisation reduce risk, enhance visibility, and protect operational continuity, just reach out.